After the FBI arrested
Cosmo, the alleged leader of the UGNazi hacking group, the hackers
attacked CloudFlare via a flaw in Google's two-factor authentication
system. The CloudFlare hack allowed UGNazi to change the DNS for 4chan,
so visitors to the site were redirected to a UGNazis Twitter account.
Hackers were able to infiltrate the
personal Gmail account of CloudFlare CEO Matthew Prince. "The attack was
the result a compromise of Google's account security procedures that
allowed the hacker to eventually access to my CloudFlare.com email
addresses, which runs on Google Apps," CloudFare's CEO Matthew Prince shared.
According to the statement on Pastebin, the hackers are not sorry for attacking 4chan.
4chan.org
is the playground that allows pedophiles to share their "collections"
and the disgusting bronies to hang out. The site is loosely monitored
and child porn threads are allowed to "stay alive" for an exceedingly
long amount of time.
Lastly, there was no
political motive here, we will not tell lies and pretend that it was all
to fight an injustice. This was for the lulz. This was for the fame.
This was done because only we have the skill to do it. This was done, so
that we can laugh at your butthurt. We did it because we can.
Prince said that no customer
credit card details were exposed since those details never pass through
its servers but go straight to a billing provider, and that it appears
the attacker had not accessed its core database or seen additional
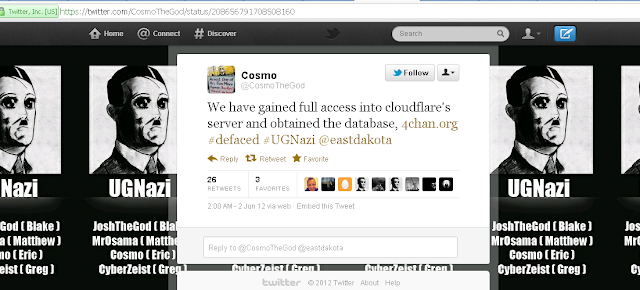
client data.However, a claim was made on the Twitter account of UGNazi
member Cosmo that UGNazi had "gained full access into Cloudflare's server and obtained the database", in a post flagging that 4Chan was redirected to the UGNazi Twitter account.
No comments:
Post a Comment